In today's
digital cellular mobile radio networks, features like power control and
handover are related to periodic measurements of level and quality at the
mobile ( downlink/forward ) and at the base station ( uplink/reverse )
receiver. The measurements values and corresponding signaling events of all
customer's calls in a specific cell under investigation could be observed by
the network operator at the protocol interface between base station controller
unit. Statistical evaluation of such mass data produced by customer calls and
collected at the protocol interface is an important aid to optimize the base
station subsystem parameters in an operating network. The almost only drawback
is that there is no exact information available about the position of the
mobile. Position determination is limited to the statement "lies in"
or "lies out" of the coverage boundaries - which are known only
roughly - of the cell under investigation.
From all
these observations, location management plays an important role in GSM mobile
system. Location management methods for mobile systems have been introduced by
Sami Tabbane, ESPTT. Several proposals have been made in the past addressing
the problems associated with the cost of location management. Overview about these
contributions will be studied first, and then the new location management
methods will be introduced.
Location
management schemes are essentially based on users' mobility and incoming call
rate characteristics. The network mobility process has to face strong
antagonism between its two basic procedures: location and paging. The location
procedure allows the system to keep the user's location knowledge, more or less
accurately, in order to be able to find him, in case of a coming call, for
example. Location registration is also used to bring the user's service profile
near its location and allows the network provide him rapidly with his services.
The paging process achieved by the system consisting of sending paging messages
in all cells where the mobile terminal could be located. Therefore, if the
location cost is high (and thus the user location knowledge is accurate), the
paging cost will be low (paging messages will be only be transmitted over a
small area) and vice versa.
I/ PRESENT LOCATION MANAGEMNET METHODS
1/ LEVEL 0: NO LOCATION MANAGEMENT
In early wide area wireless system (not yet
cellular), human operators had to process the calls and the users' locations
were not managed by the system. A user was able to generate a call through any
base station (BS), and paging messages addressed to the called mobiles were
transmitted through all BSs. The main characteristics of these systems were
very large cells, and lower user population and call rates.
Small-capacity cellular systems (with a few
tens of BSs serving a few thousand users) may also not use a location
management method, even when the standard allows it. if subscriber number and
calling rates do not require it, the location management method is not
activated; resource consumption for finding users is not so important that its
reduction is mandatory.
This level 0 method is therefore as simple as
could be: no location management is realized; the system does not track the
mobiles. A search for a called user must therefore be done over complete radio
coverage area and within a limited time. This method is usually referred to as
flooding algorithm. It is used in paging systems because of the lack of an
uplink channel allowing a mobile to inform the network of its whereabouts. It
is also used in the small private mobile networks because of their small
coverage area and user populations.
The main advantage of not locating the mobile
terminals is obviously simplicity; in particular, there is no need to implement
special databases. Unfortunately, it does not fit large networks dealing with
high numbers of users and high incoming call rates.
2/ LEVEL 1: MANUAL REGISTRATION
This method requires the user to locate himself
by achieving a special procedure if he wishes to receive his incoming calls.
From the network site, this method is relatively simple to manage because it
just requires the management of an indicator, which stores the current location
of the user. The mobile is also relatively simple; its task is just limited to
scanning the channels to detect paging messages.
This method is currently used in telepoint
cordless systems (such as CT2). The user has to register itself each time he
moves to a new island of CT2 beacons. To page a user, the network first
transmits messages through the beacon with which he registered and, if the
mobile dose not answer, extends the paging to neighboring beacons.
The main drawback of this method is the
constraint for a user to register each time he moves. Nevertheless, this low
ergonomic can be balanced by the low equipment and management costs of the
network, which allow the operator to offer users attractive fees.
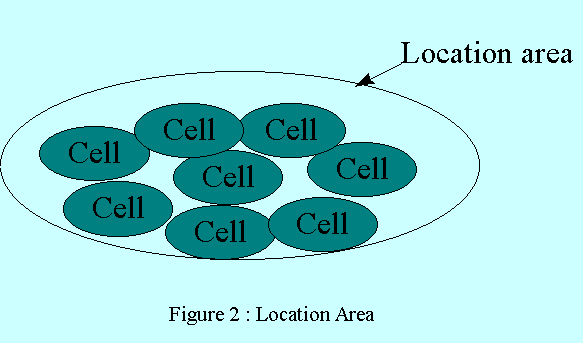
3/ LEVEL 2: USE OF LOCATION AREAS FOR AUTOMATIC
LOCATION MANAGEMENT
Presently, the location method most widely
implemented in the first- and second-generation cellular system (NMT, GSM,
IS-95, etc.) makes use of location areas (LAs) (figure 2). In these wide-area
radio networks, location management is done automatically.
Location areas allow the system to track the
mobiles during their roaming in the networks: subscriber location is known if
the system knows the LA in which the subscriber is located. When the system
must establish a communication with the mobile, the paging only occurs in the
current user LA. Thus, resource consumption is limited to this LA; paging
messages are only transmitted in the cells of this particular LA.
Implementing LA-based methods requires the use
of databases. Generally, a home database and several visitor databases are
included in the network architecture. There are also several locations updating
methods that can be implemented based on LA structuring.
a/ Periodic location updating
This method is simplest because it just
requires the mobile to periodically transmit its identity to the network. Its
drawback is its resource consumption, which is user_dependent and can be
unnecessary if the user does not move from a LA for several hours. Generally,
this method is combined with the next one.
b/ Location updating on LA crossing
This method (figure 3) first requires each BS
to periodically broadcast the identity of its LA. Second, the mobile is
required to permanently listen to network broadcast information (on the
broadcast channel) and to store the current LA identity. Of the received LA
number differs from the stored one, a location update (LU) procedure is
automatically triggered by the mobile.
The advantage of this method is that it only
requires LUs when the mobile actually moves. A highly mobile user will generate
a lot of LUs; a low mobility user will only trigger a few.
A hybrid method which combines the two previous
ones can also be implemented. The mobile generates its LUs each time it detects
a LA crossing. Nevertheless, if no communication (related to a LU or a call)
has occurred between the mobile (in idle mode, ie., powered on but not
communicating) and the network for a fixed period, the mobile generates a LU.
This periodic LU typically allows the system to recover user location data in
case of a database failure.

4/ GSM EXAMPLE
The GSM standard defines a database structure
based on:
·
An HLR (Home
Location Register) where all subscriber related information is stored (access
right, user location, etc.). Security parameters and algorithms are managed by
the authentication center (AuC) which is often considered part of the HLR.
·
Several VLRs.
Each VLR stores part of the data regarding the users located in its related
LAs.
The location management method defined in GSM
combines the periodic LU method and the LU on the border crossing. The VLR
stores the LA identifier, and the HLR stores the VLR identifier.
This consists of three main types of LU
procedures: The intra-VLR LU, the inter_VLR LU using TMSI (temporary mobile
subscriber identity), and the inter_VLR LU using IMSI (international mobile
subscriber identity). A fourth one, the IMSI attach procedure, is triggered
when the mobile is powered on in the LA where it was powered off.
In the following, we present the most complete
LU, which is inter_VLR using MISI. This procedure mainly consists of the
following steps:
·
A signaling
channel is allocated to the MS, and a LU is requested.
·
The MS provides
the network with its IMSI, which allows the new VLR (VKR2) to load
authentication data from the HLR/AuC, mainly the triplets for the
authentication and the ciphering procedures.
·
The VLR is then
able to authenticate the MS; if this step succeeds, it updates the location at
the HLR. The HLR informs the old HLR (VLR1) to remove the user's data stored in
VLR1.
·
Ciphering may be
required id available.
·
· A new TMSI is
allocated to the MS, and , after acknowledgment of its LU request ( first
message sent by the MS ), the channel finally released

5/ LIMITS OF PRESENT LOCATION MANAGEMENT
METHODS
The LA-based location management methods are
the most adapted and widely used in current cellular (GSM, IS-54 and IS-95…),
in trunk systems such as trans_European trunk radio (TETRA), in cordless
systems like Digital European Cordless Telecommunication (DECT), Personal
Access Communication System (PACS), Personal Handyphone systems (PHS), and so
on. Nevertheless, the traffic and processing generated may lead to congestion
problems in high-density systems. One of the main concerns of the system
designers is therefore to define methods allowing the system to reduce the
overhead traffic as much as possible.
Several location management methods proposed
within these last years, which attempt to reduce the overhead traffic. Followings
are location management methods for third_generation system written by Sami
Tabbane who presently teaches and performs research at ESPTT. His research
topics of interest are location management techniques, handover procedures, and
cellular networking planning.
II/ LOCATION MANAGEMENT METHODS FOR THIRD-GENERATION
SYSTEMS
He classifies the location management methods
into two major groups (figure 5). In the first, he concludes all methods based
on algorithms and network architecture, mainly on the processing capabilities
of the system. The second group gathers the methods based on learning
processes, which require the collection of statistics on users' mobility
behavior, for instance. The second method emphasizes the information
capabilities of the network.
1/ MEMORYLESS METHODS
a/ Database architecture
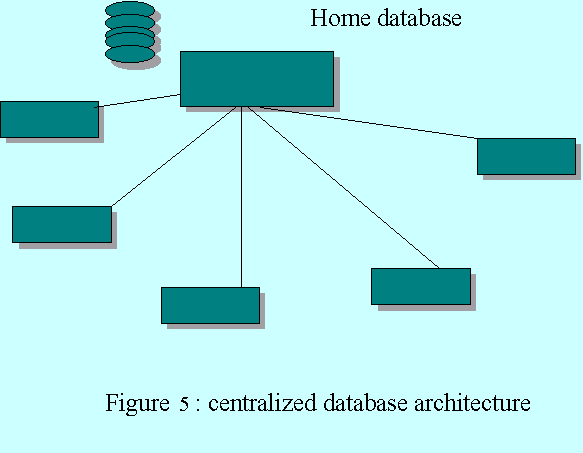
He divides into three cases:
·
Centralized
database architecture: presents an architecture where a unique centralized
database is used. This is well suited to small and medium networks, typically
based on a star topology.
·
Distributed
database architecture: uses several independent databases according to
geographical proximity or service providers. It is best suited to large
networks including subnetworks managed by different operators and service
providers. The GSM worldwide network, defined as the network made up of all
interconnected GSM networks in the world, can be such an example of a large
network. The main drawbacks of this architecture are clearly the cost of
database system acquisition, implementation, and management.

·
Hybrid database
architecture: combines the centralized and distributed architectures. In this
case, a central database (HLR-like) is used to store all user information.
Other small databases (VLR-like) are distributed all over the network. These
VLR databases store portions of HLR user records. A single GSM network is an
example of such architecture.
b/Optimizing fixed network architecture
In second-generation cellular networks and
third-generation systems, signaling is managed by the intelligent network (IN).
Appropriately organizing mobility functions and entities can help reduce the
signaling burden at the network site. The main advantage of these propositions
is that they allow us to reduce the network mobility costs independent of the
radio interface and LA organization. For example, it is proposed to use
different degrees of decentralization of the control functions. Thus, using
adapted signaling network nodes, interconnection allows mobility costs to be
reduced.
c/ Combining location areas and paging areas
In current systems, a LA is defined as both an
area in which to locate a user and an area in which to page him. LA size
optimization is therefore achieved by taking into account two antagonistic
procedures, locating and paging. Based on this observation, several proposals
have defined location management procedures, which make use of LAs and paging
areas (PAs) of different sizes. One method often considered consists of
splitting an LA into several PAs (figure 6)
An MS registers only once, that is, when it
enters the LA. It does not register when moving between different PAs of the
same LA. For an incoming call, paging messages will broadcast in the PAs
according to a sequence determined by different strategies. For example, the
first PA of the sequence can be the one where the MS was last detected by the
network. The drawback of this method is the possible delay increase due to
large LAs
d/ Multilayer LAs
In present location management methods, LU
traffic is mainly concentrated in the cells of the LA border. Based on this
observation and to overcome this problem, Okasaka has introduced the multilayer
concept. In his method, each MS is assigned to a given group, and each group is
assigned one or several layers of LAs
According to figure 6, it is clear that group 1
and group 2 MSs will not generate Lus in the same cells, thus allowing the LU
traffic load to be distributed over the cells. Nevertheless, this location
updating method, although it may help channel congestion, does not help reduce
the overall signaling load generated by LUs.
2/ MEMORY-BASED METHODS
The design of memory-based location management
methods has been motivated by the fact that systems do a lot of repetitive
actions, which can be avoided if predicted. This is particularly the case for
LUs. Indeed, present cellular systems achieved everyday, at the same peak
hours, almost the same LU processing. Systems act as memoryless processes.
Short-term and long-term memory processes can help the system avoid these
repetitive actions. Some methods have thus been proposed that be based on user
and system behavior observation and statistics.
a/ Short-term observation for dynamic LA and PA
size
In current systems, the size of LAs is
optimized according to mean parameter values, which in practical situations
vary over a wide range during the day and from one user to another.
Based on this observation, it is proposed to
manage user location by defining multilevel Lass in a hierarchical cellular
structure. At each level the LA size is different, and a cell belongs to
different LAs of different sizes. According to past and present MS mobility
behavior, the scheme dynamically changes the hierarchical level of the LA to
which the MS register. LU savings can thus be obtained.
A variant of this strategy requires from
mobiles to register in the cells where they are camped on. Registrations
involve a periodic timer which value has to be optimized. Thus rather than
paging a mobile in all cells of a LA, the mobile will be paged only in the
cells visited during the last period: these are cells the mobile camped on
during its traversal of the LA.
In figure 6, high coming call rate and
low-mobility users are directed to small LAs, medium-mobility users are
directed to medium-sized LAs, and high-velocity and low coming call rate users
are directed to large LAs.
Adapting the LA size to each user parameter
values may be difficult to manage in practical situations. This led to
definition of a method where the LAs sizes are dynamically adjusted for the
whole population, not per user as in the previous method. Statistical
information about users and mobility in the network is collected in databases
and computed. Networks characteristics in function of time, place, density, and
so on are thus evaluated. Results of this computation allow the network to
dynamically (daily, weekly, monthly, yearly.) adjust LAs sizes. For instance,
during the day, when call rates are high, it is preferable to deal with small
LAs. Conversely, at night the call rate is much lower, and therefore larger LAs
are better.
b/ Individual user patterns
Observing that users show repetitive mobility
patterns, the alternative strategy (AS) is defined; its main goal is to reduce
the traffic related to mobility management - thus reduce the LUs - by taking
advantage of users' highly predictable patterns. In AS, the system handles a
profile recording the most probable mobility patterns of each user. The profile
of the user can be provided and updated manually by the subscriber himself or
determined automatically by monitoring the subscriber's movements over period
of time.
The main savings allowed by this method are due
to the non-triggered LUs when the user keeps moving inside his profile LAs. So,
the more predictable the users' mobility, the lower the mobility management
cost.
A variant of this method, called the
Two-Location Algorithm (TLA), is proposed and studied. In this strategy, a
mobile stores the two most recently visited LA addresses. The same is done at
the HLR level. Obviously, the main advantage of this method relies on the
reduction of LUs when a mobile goes back and forth between two LAs.
c/ Predicting short-term movements of the
subscriber
The method uses a process, which predicts the
movements of the MS according to its direction, velocity, and so on. Processing
and prediction are made at both the MS and the HLR. When actual movements of
the MS do not fit with those predicted, a registration is triggered by the
mobile to inform the network of its actual location. Otherwise, no exchange is
required, which allows savings in LU processing and signaling.
d/ Mobility statistics
A mobility management method similar to AS is
defined. It is called Statistical Paging Area Selection (SPAS) and is based on
location statistics collected by each MS, which periodically reports them to
the network. These statistics consist of a list of the average duration the MS
had been located in each LA. A priority rule is determined to settle the
sequence of LAs visited by the mobile. If this sequence id different from the
last one reported to the network, the MS transmits it; otherwise, nothing is
done. The paging process is achieved in the same way as in AS. When the MS
moves to an area that is not on the reported list, it has to process a
temporary location registration to the network.
In " A Predictive Mobility Management
Algorithm for Wireless Mobile Computing and Communications ', G. Y. Liu and G.
Q. Maguire proposed the method provide a means of allowing preconnection and
pre-assignment of data or services at the location before the user moves into
it, so he can immediately receive service or data. This method clearly applies
to location management. Just as are the previous two methods, it is based on
users' movement history patterns. Called Mobile Motion Prediction (MMP), it
allows the system to predict the future location of the user. Schematically,
the MMP combines two movement models: Movement circle (MC), based on a
closed-circuit model of user movement behavior, and Movement Track, used to
predict routine movements. MC is used to predict long-term regular movements.
The author, finally,
mentions the method proposed in " Comparing the PCSS Location Tracking
Strategies" by Y. B. Lin and S. Y. Hwang. The method makes use of a cache
memory for reducing the search cost. The proposal is to store the location of
the frequently called mobiles in a local database (i.e. cache). This scheme
allows the number of queries to the HLR to be reduced; thus reducing the
signaling traffic at he fixed network side between the local database and the
HLR.
 Spolecenske hry skladem
Spolecenske hry skladem